電驢下載基地 >> 软件资源 >> 系統工具 >> 《磁盤工具軟件(安全刪除敏感數據)》(O&O Software SafeErase )Server|Workstation v5.1.672 x86|x64[壓縮包]
| 《磁盤工具軟件(安全刪除敏感數據)》(O&O Software SafeErase )Server|Workstation v5.1.672 x86|x64[壓縮包] | |
|---|---|
| 下載分級 | 软件资源 |
| 資源類別 | 系統工具 |
| 發布時間 | 2017/7/11 |
| 大 小 | - |
《磁盤工具軟件(安全刪除敏感數據)》(O&O Software SafeErase )Server|Workstation v5.1.672 x86|x64[壓縮包] 簡介: 中文名 : 磁盤工具軟件(安全刪除敏感數據) 英文名 : O&O Software SafeErase 資源格式 : 壓縮包 版本 : Server|Workstation v5.1.672 x86|x64 發行時間 : 2012年 制作發行 : O&O Software GmbH 地區 : 德國 語言 : 英文 簡介 : O&O 的磁盤工具軟件,可以絕對安全的刪除
電驢資源下載/磁力鏈接資源下載:
- 下載位址: [www.ed2k.online][磁盤工具軟件(安全刪除敏感數據)].OO.Software.SafeErase.Server.v5.1.672.Incl.Keygen-Lz0.zip
- 下載位址: [www.ed2k.online][磁盤工具軟件(安全刪除敏感數據)].OO.Software.SafeErase.Server.v5.1.672.X64.Incl.Keygen-Lz0.zip
- 下載位址: [www.ed2k.online][磁盤工具軟件(安全刪除敏感數據)].OO.Software.SafeErase.Workstation.v5.1.672.Incl.Keygen-Lz0.zip
- 下載位址: [www.ed2k.online][磁盤工具軟件(安全刪除敏感數據)].OO.Software.SafeErase.Workstation.v5.1.672.X64.Incl.Keygen-Lz0.zip
全選
"《磁盤工具軟件(安全刪除敏感數據)》(O&O Software SafeErase )Server|Workstation v5.1.672 x86|x64[壓縮包]"介紹
中文名: 磁盤工具軟件(安全刪除敏感數據)
英文名: O&O Software SafeErase
資源格式: 壓縮包
版本: Server|Workstation v5.1.672 x86|x64
發行時間: 2012年
制作發行: O&O Software GmbH
地區: 德國
語言: 英文
簡介:

O&O 的磁盤工具軟件,可以絕對安全的刪除敏感文件和資料,刪除後不可恢復。原因是 SafeErase 不僅僅表面上刪除了文件名,並且會把文件占用的空間全部充0 ,這樣那些黑客和寫偷竊數據的“間諜”也只能望盤興歎。SafeErase 有點特別,不像大部分軟件一樣,它本身沒有一個程序供你運行,而是完全集成到資源管理器中。只要你在資源管理器中選用 SafeErase 功能,安全刪除操作就可以開始。
Windows與數據恢復方案中,該軟件容易恢復被刪除的任何信息。另一方面,有幾種文件粉碎機方式徹底清除收不回的文件。 O&O SafeErase 是一個眾所周知的文件管理和隱私保護軟件。
O&O SafeErase,您可以使用國際認可和推薦的方法安全地刪除單個文件夾以及整個電腦內容。這些技術有些是授權自於美國國防部國防部(DoD)和德國信息安全技術部(BSI)的。
O&O SafeErase也同時保護您的隱私,每次你上網,你的活動痕跡包括網站的訪問和您的個人資料,點擊O&O SafeErase安全刪除所有這些痕跡了。
O&O SafeErase 是從硬盤安全刪除敏感數據的解決方案,為你的私人方面提供最終的保護。僅單擊鼠標,就可以永久地安全刪除文件,文件夾及分區。無論是過期的財務信息,電子郵件檔案或個人檔案,O&O SafeErase 都可以保證將這些數據永久刪除。這是因為 O&O SafeErase 並不僅僅是刪除數據,而是利用5個公認推薦的刪除方法將數據徹底清除。
O&O SafeErase主要特點
- 網絡安全:安全刪除浏覽器數據
- 預先定義的配置文件
- 各種設定為安全刪除
- 關於刪除程序的詳細報告
- 零覆蓋(快速刪除)
- 支持多核心處理器
- 清晰的用戶顯示界面
- 安全刪除文件和分區
- 安全刪除整個電腦
- 安全移動文件和目錄
- 六個安全地刪除您機密數據的方法
- 完全集成在Windows
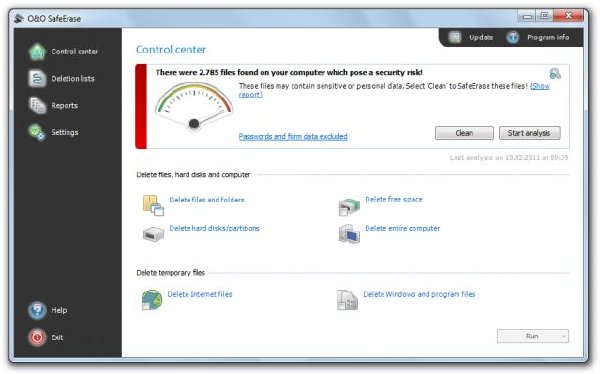
No chance for data spies
What happens to your old computer or hard drive when you get a new one? Do you return your company’s computers to the leasing company or even sell your laptop on the Internet? In that case, there are good chances that complete strangers might gain access to your private pictures, letters or business secrets.
The fact of the matter is, data deleted using Windows is not really deleted! Unauthorized persons can still recover your digital pictures as well as your personal and company data, even if you formatted the disk beforehand. Surfing the Internet leaves its mark as well: On the basis of the Internet browsing history stored on your computer, it’s easy to generate an accurate profile of your preferences, see the pages you’ve visited, and even scan the files you’ve downloaded. Protect yourself by using O&O SafeErase to permanently delete all data from your hard disk using scientifically recognized methods.
The analysis tool of O&O SafeErase 5 lets you track down and immediately remove all the files that are a security risk on your computer. What’s more, data from SSDs can now be permanently deleted as well using methods that go sparingly on resources. Never take chances with your data: SafeErase it!
Important Features at a Glance
SafeErasing:
- Files, folders and individual partitions
- Memory cards and USB data volumes
- Free hard disk space
- Entire computer, no boot medium necessary
- Internet and temporary program files
Securely move files and folders
Six methods to permanently delete sensitive data
Complete integration into Windows Explorer
Detailed reports as proof of deletion
Speed optimization of deletion processes
NEW: Analysis tool to search for unsafely deleted files
NEW: Adapted deletion method for SSDs
NEW: Enhanced report and activity management
Complete protection of your confidential data
Your company’s servers are the places where all internal information such as customer data and the figures for the sales and bookkeeping departments are gathered. That also goes for the backups containing vital information collected over years. If you ever decide to replace a single disk or an entire server with a new one, the information contained on your old material can quickly turn into a major security risk.
Protect yourself by letting O&O SafeErase permanently delete your worn out disks using scientifically recognized methods. There are a total of six deletion methods available to you, each one offering its own special type of deletion and level of security.
Remember: Even when you’ve formatted a disk with Windows before disposing of it or returning it to the leasing company, data spies can still recover and misuse your data easily using standard data recovery software. Never take chances with your data: SafeErase it!
Important Features at a Glance
Permanent deletion of:
-Files, folders and individual partitions
-Memory cards and USB data volumes
-Free hard disk space
-Entire computer, no boot medium necessary
-Internet and temporary program files
Securely move files and folders
Six methods to permanently delete sensitive data
Complete integration into Windows Explorer
Detailed reports as proof of deletion
Speed optimization of deletion processes
NEW: Analysis tool to search for unsafely deleted files
NEW: Adapted deletion method for SSDs (TRIM)
NEW: Enhanced report and activity management
NEW: Enhanced command processing via command line
NEW: Optimized for server systems
NEW: Deletes multiple disks simultaneously
代碼
英文名: O&O Software SafeErase
資源格式: 壓縮包
版本: Server|Workstation v5.1.672 x86|x64
發行時間: 2012年
制作發行: O&O Software GmbH
地區: 德國
語言: 英文
簡介:

O&O 的磁盤工具軟件,可以絕對安全的刪除敏感文件和資料,刪除後不可恢復。原因是 SafeErase 不僅僅表面上刪除了文件名,並且會把文件占用的空間全部充0 ,這樣那些黑客和寫偷竊數據的“間諜”也只能望盤興歎。SafeErase 有點特別,不像大部分軟件一樣,它本身沒有一個程序供你運行,而是完全集成到資源管理器中。只要你在資源管理器中選用 SafeErase 功能,安全刪除操作就可以開始。
Windows與數據恢復方案中,該軟件容易恢復被刪除的任何信息。另一方面,有幾種文件粉碎機方式徹底清除收不回的文件。 O&O SafeErase 是一個眾所周知的文件管理和隱私保護軟件。
O&O SafeErase,您可以使用國際認可和推薦的方法安全地刪除單個文件夾以及整個電腦內容。這些技術有些是授權自於美國國防部國防部(DoD)和德國信息安全技術部(BSI)的。
O&O SafeErase也同時保護您的隱私,每次你上網,你的活動痕跡包括網站的訪問和您的個人資料,點擊O&O SafeErase安全刪除所有這些痕跡了。
O&O SafeErase 是從硬盤安全刪除敏感數據的解決方案,為你的私人方面提供最終的保護。僅單擊鼠標,就可以永久地安全刪除文件,文件夾及分區。無論是過期的財務信息,電子郵件檔案或個人檔案,O&O SafeErase 都可以保證將這些數據永久刪除。這是因為 O&O SafeErase 並不僅僅是刪除數據,而是利用5個公認推薦的刪除方法將數據徹底清除。
O&O SafeErase主要特點
- 網絡安全:安全刪除浏覽器數據
- 預先定義的配置文件
- 各種設定為安全刪除
- 關於刪除程序的詳細報告
- 零覆蓋(快速刪除)
- 支持多核心處理器
- 清晰的用戶顯示界面
- 安全刪除文件和分區
- 安全刪除整個電腦
- 安全移動文件和目錄
- 六個安全地刪除您機密數據的方法
- 完全集成在Windows


No chance for data spies
What happens to your old computer or hard drive when you get a new one? Do you return your company’s computers to the leasing company or even sell your laptop on the Internet? In that case, there are good chances that complete strangers might gain access to your private pictures, letters or business secrets.
The fact of the matter is, data deleted using Windows is not really deleted! Unauthorized persons can still recover your digital pictures as well as your personal and company data, even if you formatted the disk beforehand. Surfing the Internet leaves its mark as well: On the basis of the Internet browsing history stored on your computer, it’s easy to generate an accurate profile of your preferences, see the pages you’ve visited, and even scan the files you’ve downloaded. Protect yourself by using O&O SafeErase to permanently delete all data from your hard disk using scientifically recognized methods.
The analysis tool of O&O SafeErase 5 lets you track down and immediately remove all the files that are a security risk on your computer. What’s more, data from SSDs can now be permanently deleted as well using methods that go sparingly on resources. Never take chances with your data: SafeErase it!
Important Features at a Glance
SafeErasing:
- Files, folders and individual partitions
- Memory cards and USB data volumes
- Free hard disk space
- Entire computer, no boot medium necessary
- Internet and temporary program files
Securely move files and folders
Six methods to permanently delete sensitive data
Complete integration into Windows Explorer
Detailed reports as proof of deletion
Speed optimization of deletion processes
NEW: Analysis tool to search for unsafely deleted files
NEW: Adapted deletion method for SSDs
NEW: Enhanced report and activity management
Complete protection of your confidential data
Your company’s servers are the places where all internal information such as customer data and the figures for the sales and bookkeeping departments are gathered. That also goes for the backups containing vital information collected over years. If you ever decide to replace a single disk or an entire server with a new one, the information contained on your old material can quickly turn into a major security risk.
Protect yourself by letting O&O SafeErase permanently delete your worn out disks using scientifically recognized methods. There are a total of six deletion methods available to you, each one offering its own special type of deletion and level of security.
Remember: Even when you’ve formatted a disk with Windows before disposing of it or returning it to the leasing company, data spies can still recover and misuse your data easily using standard data recovery software. Never take chances with your data: SafeErase it!
Important Features at a Glance
Permanent deletion of:
-Files, folders and individual partitions
-Memory cards and USB data volumes
-Free hard disk space
-Entire computer, no boot medium necessary
-Internet and temporary program files
Securely move files and folders
Six methods to permanently delete sensitive data
Complete integration into Windows Explorer
Detailed reports as proof of deletion
Speed optimization of deletion processes
NEW: Analysis tool to search for unsafely deleted files
NEW: Adapted deletion method for SSDs (TRIM)
NEW: Enhanced report and activity management
NEW: Enhanced command processing via command line
NEW: Optimized for server systems
NEW: Deletes multiple disks simultaneously
代碼
LineZer0! ² ² ²
²²² ² ² ²² ² ²±
±²² ² ²²²² ²²²
² ² ² ² ² ²²
² ²² ² ² ²²² ² ²
²² ²² ² ²²² ²² ² ²
² ²²² ² ²²² ²² ±² ²²±
² ² ²²² ²²² ²²±
² ±² ² ²² ²²²²± ± ²
² ²°² ² ² ²²² ² ± ²²
² ² ²² ² ²² ² ² ²
²² ² ²²²² ² ² ² ²²
²² ²²² ² ² ² ²²² ²²± ²²
²²² ² ²²² ²²²
cpN²²² ±² ²²±±²²²²²°² ²± ²²²cRo
²² ±²²²²² ²²² ²²²²²²²± ²²
²²²² ±±²²²²² ² ²² ²² ²²²²²±± ²²²²
² ²² ²²²² ²² presents ² ²±²² ²² ²
²² ² ²² ² ² ²²
²² ²²± ² ² ² ±²² ²²
²² °° °° ²²
² ²
² SafeErase.Server v5.1.672 ²
²²² Release Date : 2012-02-22 ²²²
²² Nfo Date : 2012-02-22 ²²
²² ² ² ²²
² Num. Disks : xx/08 OS : Windows ²
² Nfo Time : 13:37 Rel Type : Keygen ²
² Cracker : Team Lz0 Archive : lz0*.zip ²
² Packer : Team Lz0 Rating : Your choice ²
² Supplier : Team Lz0 Language : English ²
² Protection : N/A ²
² ²
² Requirements : N/A ²
² : Always use a firewall. ²
² Publisher URL : http://www.oo-software.com ²
² Publisher : OO Software ²
² ²
² (-) Keyfile / License (-) Emulator ²
² (-) Patch (-) Serial ²
² (-) Cracked .EXE / .DLL (-) Retail ²
² (x) Keygen (-) Trainer ²
² ² (-) Loader (-) Other ² ²
² ² ² ²
²² ²²
²² ² 1999 - 2012 ² ²²
² ²² °°° °°° ²² ²
²²² ² ² °±± ²² ±±° ² ² ²²²
²²² ² ±²² ²²± ² ²²²
²² ²²²² + I N F O + ²²² ²²
²² ² ²²²² ² ² ²²
² ²
² The consequences of sensitive corporate data falling into the ²
² wrong hands, be it competitors or even the public, might cause ²
² serious and lasting damages or even mean the end of your ²
² company. OandO SafeErase allows you to permanently delete ²
² sensitive data from your server by using approved procedures, ²
² so that a reconstruction is no longer possible - even if using ²
² special software or a data recovery lab. ²
² ²
² ² ² ²
²² ²²
² ²² ²² ²
² ²² °°° °°° ²² ²
²²² ² ² °±± ²² ±±° ² ² ²²²
²²² ² ±²² ²²± ² ²²²
²² ²²²²+ I N S T A L L +²²² ²²
²² ² ²²²² ² ² ²²
² ²
² 1) Unpack and install. ²
² 2) Use the key generator to generate a valid serial. ²
² 3) Enjoy this release! ²
² ²
² NOTE: For obvious reasons you should always make sure that ²
² the title is restricted access to internet by a firewall ²
² to avoid any problems. Further, when running our ²
² keygens/patches you might need to run it with admin ²
² rights while in Vista/Win7 to ensure that it has ²
² enough privileges. ²
² ²
² ² ² ²
²² ²²
² ²² ²² ²
² ²² °°° °°° ²² ²
²²² ² ² °±± ²² ±±° ² ² ²²²
²²² ² ±²² ²²± ² ²²²
²² ²²²² + J O I N + ²²² ²²
²² ² ²²²² ² ² ²²
² ²
² So you are interested in joining one of the most successful ²
² groups of all time? Then you might want to continue reading. ²
² Not only can we offer whatever your heart might desire, but ²
² becoming part of the group will also be one of the more ²
² significant decisions you perhaps will take. ²
² ²
² Ever since our beginning in 1999 we’ve strived to make a group ²
² that not only is a group of knowledge, but a gathering of ²
² people that wants friendship, devotion, respect and fun. Hard ²
² work is what has brought us where we are today, and hard work ²
² is also what we would expect from you. ²
² ²
² Given the amount of hours we all put into this every day, we ²
² like to see our self as a secondary family. We strive to take ²
² care of each other and thus – mutual respect is the essence of ²
² our group. We never pushed for being elite, as we do not believe ²
² that any of us deserve the mark of the elitists. Every member ²
² of our group is taught to honor the next guy or gal with the ²
² same respect as he or her demands for themselves. The same ²
² thought applies to how we look at other groups. ²
² ²
² Are you ready to become part of a family? Do you think you have ²
² what it takes? Then now is the time to get up and contact us. ²
² Perhaps you will find a new road to follow with us. Open ²
² positions are as follows, but if you do feel you have something ²
² to contribute with but feel that it doesn’t match any of the ²
² open positions, then do contact us and let us be the judge ²
² of that. ²
² ²
² CRACKERS ²
² Do you have a thrill to find solutions to various protection ²
² schemes? May it be unpacking, patching, finding algorithms ²
² or emulating? We’re always open for individuals that want to ²
² expand their knowledge in reversing. You are required to have ²
² some former knowledge in reversing as we do not tutor people ²
² from scratch. Former experience from other scene groups is ²
² good, but not a necessity. Unsure if you qualify? Contact us, ²
² and we’ll decide based on your qualities. Be prepared that ²
² we will demand examples of previous work. ²
² ²
² CODERS ²
² You’re enthusiastic about coding, you love to optimize and ²
² integrate various projects; we always have projects ranging ²
² from smaller ones to large ones that are in need of attendance. ²
² If you are joining our family as a coder you will be appointed ²
² a variety of projects that will push you to do your best and ²
² will probably also serve as a great way of becoming an even ²
² greater coder. Projects are ranging from database integrations, ²
² IRC bots, and cracktros to tools and security oriented ²
² development. Examples of previous work will be required and ²
² experience beyond 2 years is also a requirement. ²
² ²
² SUPPLIERS ²
² Do you have access to good titles? Perhaps you work as an ²
² engineer, network administrator, or by any other means can ²
² acquire the latest versions of what you have access to? Then ²
² feel free to contact us and let us know what you have. We do ²
² not focus on anything in particular and as such you will find ²
² that we do titles ranging from CAD/CAM to more common graphics, ²
² music and programming titles – as well as ordinary shareware ²
² titles. Contact us today and we will see if your titles are ²
² something we’d like to put some effort into. ²
² ²
² SITES ²
² You’ve been running a dedicated and well supported site for ²
² more than 6 months, the site has grown some reputation and your ²
² staff as well as the chosen link location is security oriented. ²
² We do not accept sites that are running of rented boxes; ²
² neither do we accept sites located in United States of America, ²
² Germany or Austria. The speed of the site does not matter, what ²
² do matter is that it’s stable, it’s secure and above all – the ²
² entire site as well as crew is operating encrypted. You feel ²
² that this might be you? Then let us know today, and we will ²
² be getting back to you shortly. ²
² ²
² BOX OPERATORS ²
² You have been running hosting services for years; either being ²
² BNC solutions or IRC daemons – or perhaps just have some boxes ²
² that you might think we can use. You’re an administrator of a ²
² network and have complete control over the box, the network ²
² area and access levels. If so, then you are someone we are ²
² interested to talk to. Keep in mind that we do not offer any ²
² boxes residing in the same countries as mentioned under “SITES”. ²
² ²
² Remember, we all started out somewhere so do not keep yourself ²
² from contacting us thinking you aren’t good enough to help out, ²
² let us decide that. ²
² ²
² ² ² ²
²² ²²
² ²² ²² ²
² ²² °°° °°° ²² ²
²²² ² ² °±± ²² ±±° ² ² ²²²
²²² ² ±²² ²²± ² ²²²
²² ²²²² + L E G A L + ²²² ²²
²² ² ²²²² ² ² ²²
² ²
² Our releases are made to make sure that the end-user is able ²
² to fully test a title before going into a purchase as well as ²
² give the end-user an opportunity to make backup copies of ²
² titles he or she already owns. Please do respect our stance ²
² on this and make sure that you buy the required licenses upon ²
² deciding to buy the product. Respect the software authors ²
² that have put time, money and effort into creating the title ²
² you now have in your hand. ²
² ²
² 1. You should only use this title for the period of time ²
² as you decide if this is the right product for you ²
² personally or for your business. Upon deciding ²
² that this is the product you are looking for then ²
² we encourage you to buy the necessary licenses. ²
² ²
² 2. If you already own this title then this release can be ²
² used as a substitute to the original disks for backup ²
² and archiving purposes. This is convenient if you ²
² own a large set of various titles that all require ²
² dongles to run and you keep on mixing up the dongles. ²
² Our releases have removed those checks and thus will ²
² be more convenient to use. Again, this should only ²
² be the case if you own the required licenses. ²
² ²
² 3. We do not wish for our releases to be widely spread ²
² across web boards, P2P networks and the like. While we ²
² do know that occurs we strongly urge people to not ²
² share these titles at such places. ²
² ²
² 4. The group is not involved with the spreading of the ²
² release, partial files or any of the cracks. The ²
² distribution of our releases are all done by third ²
² parties – and as such according to the laws of the ²
² countries where our members reside, it is not our ²
² responsibility what others decides to do with ²
² these releases. ²
² ²
² 5. You are NOT allowed to distribute our titles with the ²
² intent of earning money. This title is not yours to ²
² sell. We, as a group, do not participate in such ²
² actions and we plead to those that are thinking about ²
² selling pirated titles, reconsider – not only are you ²
² hurting us seeing our releases being abused, but above ²
² all – you are actually stealing profit from the ²
² software authors. ²
² ²
² 6. We do not take any responsibility of computer or data ²
² loss that may occur from using our releases. Keep in ²
² mind that you are using a third party solution that ²
² does not come from the original software authors. ²
² However we strive to make perfect releases so the ²
² chances of something like that happening are slim. ²
² ²
² 7. The usage of our cracks is legal in most countries ²
² outside of the United States, if and only if you own a ²
² complete copy of the program or game. But you are ²
² required to read the end user license agreements (EULAs) ²
² that comes with the various titles to be sure that you ²
² are not violating any agreements. ²
² ²
² According to the DMCA ACT in the United States you have no ²
² rights to circumvent any copy protection. Keep this in mind ²
² as the penalties for doing so there are harder than if you ²
² stole the actual title from the self. Our base of operation ²
² however is not located in the states, and thus we are not ²
² bound by any of the legislations like “no electronic theft act” ²
² “digital millennium copyright act” or “the patriot act”. But ²
² you as a end-user might be, so be certain to read the EULAs ²
² that you agree to upon installing something to make sure ²
² you are not breaking any domestic laws. ²
² ²
² Finally, we do encourage you to explore the open source ²
² community. In most cases you will find open and free software ²
² that does exactly what you need, and it won’t cost you ²
² anything. At the same time you can enjoy the feeling of ²
² doing something good, and support the open source community. ²
² ²
² By using this release you agree to the statement written above, ²
² and accept that the responsibility to whet ever the usage of ²
² this title is legal or not is with you and you only. Make sure ²
² that you understand the potential risks of using this release. ²
² ²
² ² ² ²
²² ²²
² ²² ²² ²
² ²² °°° °°° ²² ²
²²² ² ² °±± ²² ±±° ² ² ²²²
²²² ² ±²² ²²± ² ²²²
²² ²²²² + G R E E T S + ²²² ²²
²² ² ²²²² ² ² ²²
² ²
² HERiTAGE, RAZOR1911, F4CG, EMPHASiS, ZENiTH, MYTH ²
² GHOST RiDERS, LEGENDS NEVER DiE, ENFUSiA, BiN ²
² FATiGUED COURiERS NETWORK (FCN) ²
² ² CHEMiCAL REACTiON (CRO) ² ²
²² ²²
² ²² ²² ²
² ²² °°° °°° ²² ²
²²² ² ² °±± ²² ±±° ² ² ²²²
²²² ² ±²² ²²± ² ²²²
²² ²²²²+ C O N T A C T +²²² ²²
²² ² ²²²² ² ² ²²
² ²
² If you want to contact the group either for a open membership ²
² position, for a site offer or just want to let us know that ²
² some release might be flawed, then we welcome your response. ²
² However we do not send out releases, files from releases, ²
² cracks or information to where you might find this. For quick ²
² response you might want to search for us online, if you can ²
² manage to wait then send us an email on the address below. ²
² ²
² ² EMAIL : [email protected] ² ²
² ² UPDATED : 4th of November 2011 ²
²² ²²
² ²
² ² ² ²
² ²
² ²²² °°° °°° ²²² ²
² ² ² °±± ²² ²² ±±° ² ² ²
² ±²² ²²± ²
²²²²²² ²²²²²²
²²² ascii proudly done ²²²²
²² by cpN of cRo ²²
²² in 2oo6 ²²
² ²
²² ² ² ²²
²²² ² ²²²
² ²
²²
²
相關資源:
- [應用軟件]《Mindgenius business 2005》15.0.0.591[安裝包]
- [編程開發]《G3D革新游戲引擎》(G3D Innovation Engine )9.0[壓縮包]
- [編程開發]《可視化編程》(Mictosoft Visual Studio 6.0)Visual Studio 6.0[ISO],編程開發、資源下載
- [系統工具]《Acronis系統備份還原工具》(Acronis.True.Image.Home.2011)v14.0.0.6574+v14.0.6857[壓縮包]
- [軟件綜合]【更新以前種子】[音高修復效果器].Antares.Autotune.EVO.v6.09.VST
- [應用軟件]《數學軟件FreeMat》(FreeMat&FreeMatPortable)4.0[安裝包]
- [多媒體類]《高清視頻轉換工具》(WinX HD Video Converter Deluxe)v3.12.5[壓縮包]
- [系統工具]《東石®備份還原9專業版》(FarStone TotalRecovery Pro)v9.02[壓縮包]
- [應用軟件]ChemDraw
- [網絡軟件]《鎖定:怒火危崖2》(Lock On: Flaming Cliffs 2)破解版[光盤鏡像] 免費下載
- [游戲周邊]《《碧之軌跡》中文完全攻略(掃描版)》更新完畢[壓縮包]
- [硬盤游戲]《實況足球:職業進化足球2015》(Pro Evolution Soccer 2015)免安裝硬盤版[壓縮包]
- [人文社科]《著作權合理使用制度研究》(吳漢東)掃描版[P
- [生活圖書]《PHOTOSHOP人像攝影與後期處理精粹》全彩版[PDF]
- [其他圖書]《梅西耶天體觀測指南》(Atlas of the MESSIER OBJECTS HIGHLIGHTS OF THE DEEP SKY)[PDF]
- [電腦基礎]《mac的基礎視頻教程》[壓縮包]
- [其他圖書]《魯迅全集 (PDF)共二十卷》人民文學出版社
- [藝術體育]《拉法百場英超比賽》(Rafas Top 100 EPL Games)[光盤鏡像]
- [人文社科]《包豪斯理想》清晰掃描版[PDF]
- [人文社科]《中國科技批評史》(朱亞宗)掃描版[PDF]
- 《易我分區大師專業版》(EaseUS Partition Master)v9.1.0.Professional.Edition[壓縮包]
- 《SLICTool傻瓜工具包》(SLICTools)綠色版(內附超詳細教程)[壓縮包]
- 《東石®備份還原9專業版》(FarStone TotalRecovery Pro)v9.0[壓縮包]
- 《虛擬系統》(VMware Workstation)v7.1.2.301548 Linux[壓縮包]
- 《系統優化工具》(Bitsum Technologies Process Lasso Pro)v6.0.1.74 x86|x64[壓縮包]
- 《 軟件卸載程序》(Perfect Uninstaller )v6.3.3.9 [壓縮包]
- 《全系統備份軟體》(Acronis True Image Home v11)英文版/德語版
- 《磁盤碎片整理工具》(O&O Defrag Professional )v16.0.183 x86|x64[壓縮包]
- 《Acronis系統備份還原工具》(Acronis True Image Home 2012)更新Plus Pack/含注冊碼[壓縮包]
- 《Hetman分區恢復工具》(Hetman Partition Recovery)v1.0[壓縮包]
- 《系統移植工具》(Paragon Adaptive Restore for Drive Backup)V9 Professional[光盤鏡像]
- 《磁盤碎片整理工具》(Advanced Defrag)v4.5.0.datecode.20100518/WinAll/含注冊機[壓縮包]
免責聲明:本網站內容收集於互聯網,本站不承擔任何由於內容的合法性及健康性所引起的爭議和法律責任。如果侵犯了你的權益,請通知我們,我們會及時刪除相關內容,謝謝合作! 聯系信箱:[email protected]
Copyright © 電驢下載基地 All Rights Reserved



